Credential Management for IT Automation? Here’s Why It’s Necessary.
A manual approach to credential management is slow and disorganized, which is why ActiveBatch has partnered with the CyberArk Application Access Manager.

By the IT Automation Editorial Staff in conjunction with CyberArk
Do We Need Credential Management?
2.3 billion credentials were stolen in 2017, affecting a variety of industries, according to the 2018 Credential Spill Report.
How did hackers gain access to 2.3 billion accounts? Because, despite repeated warnings, organizations are not as careful with their passwords as they should be.
OpenVPN has found that a whopping 25% of US employees use the same password for each of their accounts —and to make matters worse, most of them don’t password-protect their devices.
It might seem like a simple request, to ask that employees rotate their passwords —all of their passwords— every 90 days. But consider that the average employee needs a password to access 191 applications, devices, platforms, accounts, environments, and more, according to the 2018 Global Password Security Report.
Rotating 191 logins isn’t something you can take care of at lunch.
Trouble Integrating Your IT Automation Solution with Your Credential Management Platform?
Find out how the CyberArk integration for ActiveBatch streamlines credential management
Taking a manual approach to credential management can be time-consuming, cumbersome, and disorganized, and because of this, many organizations are turning to third-party platforms that automate and centralize credential management across the business.
Privileged access security (PAS) tools allow users to centrally store passwords and credentials within a secure vault where passwords are routinely rotated or randomized. By automating this task, PAS tools can remove human-error from the process while saving employees time that would otherwise be spent manually updating dozens of passwords.
PAS solutions also facilitate the removal of hard-coded credentials from legacy and custom applications while providing full audit and response capabilities to help ensure proper access. This allows organizations to secure, protect, and monitor privileged credentials, reducing the chances of a cyber-attack or data breach while taking unwieldy tasks out of the hands of human administrators.
However, automated credential management processes can hinder IT Automation efforts by making it more challenging to integrate disparate IT technologies, applications, databases, platforms, and more.
One work-around is to develop scripts that allow the PAS tool to pass rotated passwords to the IT Automation solution. But this could potentially require dozens of error-prone scripts for each tool the IT Automation solution needs to access.
A better solution is to integrate the PAS tool with the IT Automation solution, removing silos and providing scalable, improved security.
ActiveBatch’s Certified Integration with CyberArk
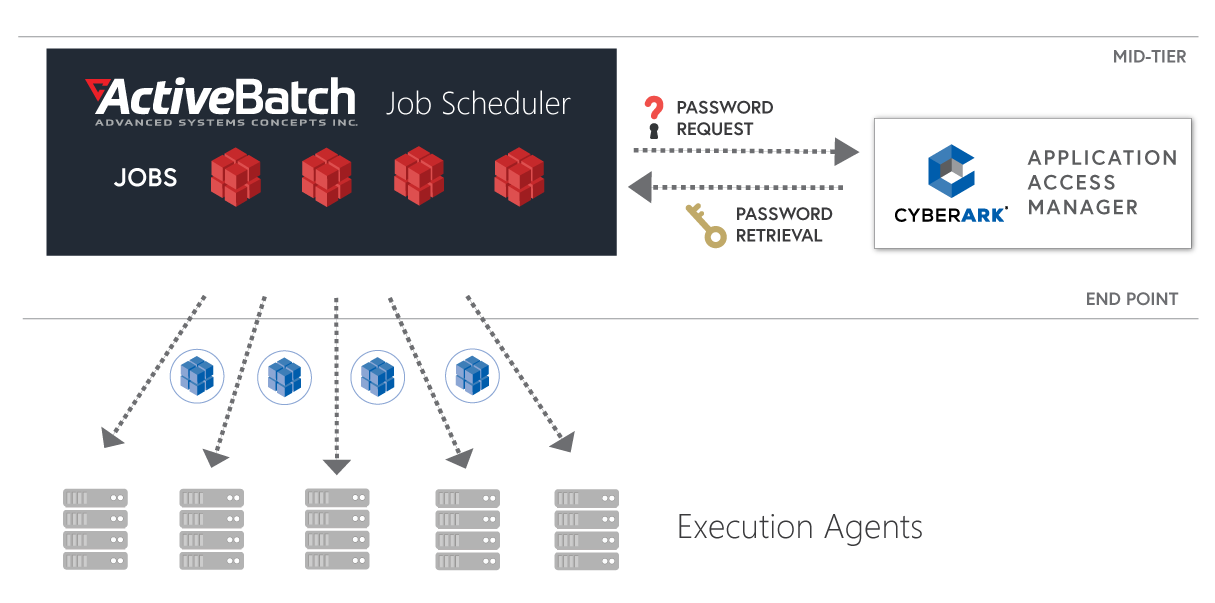
In order to provide IT with a powerful automation solution that supports scalable credential management, ActiveBatch has collaborated with CyberArk, providing an out-of-the-box integration with the CyberArk Application Access Manager solution.
This integration allows ActiveBatch workflows to dynamically retrieve credentials from CyberArk at runtime, prior to dispatching Jobs and Agents.
About CyberArk
CyberArk is the global leader in privileged access security, a critical layer of IT security to protect data, infrastructure and assets across the enterprise, in the cloud and throughout the DevOps pipeline. CyberArk delivers the industry’s most complete solution to reduce risk created by privileged credentials and secrets. To learn more, visit www.cyberark.com
With ActiveBatch’s CyberArk integration, credential retrievals are triggered whenever an ActiveBatch Job requires credentials from CyberArk. ActiveBatch also offers a prebuilt, pretested Job Step that securely retrieves and passes credential information for use in subsequent workflow steps.
This means that IT can harness ActiveBatch’s powerful automation capabilities while extending CyberArk’s cybersecurity benefits to the IT Automation environment.
IT needs automation and credential management. With ActiveBatch and CyberArk, IT can now have both.